This page describes how to use the telnet/ssh client PuTTY. Using ssh encrypts your data so that it cannot be read off the internet by other people as it passes through other machines.
Using ssh and Putty.
[NOTE: Use port 222 for access to all CSE lab workstations]
- Open PuTTY
- Launch PuTTY
- Enter server - select protocol
- Accept host key
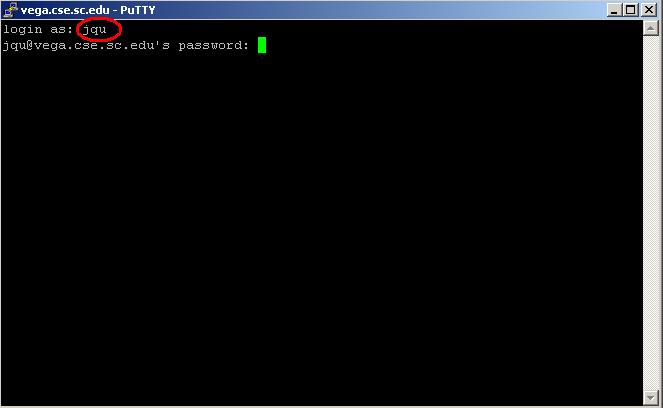
- Enter username and password
- UNIX!
Related Documents
- advanced PuTTY -- Reasons to use PuTTY, configuring PuTTY, saving sessions in PuTTY, doing cool things with PuTTY ...and "more"
Using PuTTY/ssh
1. Open PuTTY Download putty.exe from https://www.putty.org/ to your computer. NOTE: This file is NOT an installer, it is the whole program. PuTTY is small enough and simple enough that it does not require an installer.
2. Launch PuTTY Double-click on the putty icon:
to launch the PuTTY Configuration window:
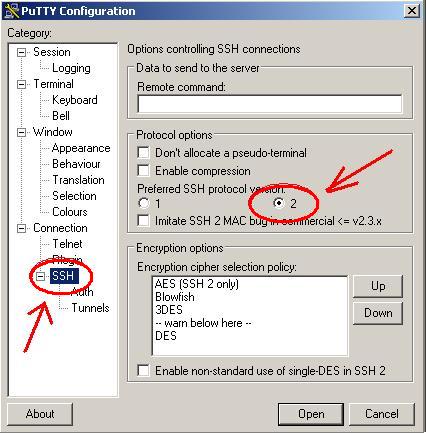
3. Select SSH version - SSH version 2
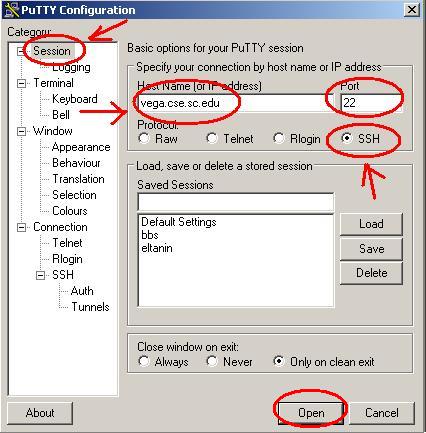
4. Enter server - select protocol Enter vega.cse.sc.edu (You can type any UNIX host name) in the field for 'Host Name (or IP address)' and select 'SSH' for the 'Protocol:'
[NOTE: use port 222 for all CSE lab workstations.]
Then simply press the 'Open' button.
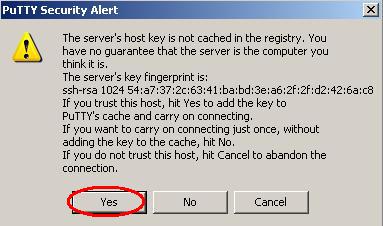
5. Accept host key If this is the first time you have connected to this server, a window will pop up that asks you about the server's host key being cached in the registry. Why does it do this and what do you press?
Long Answer: This is ssh telling you that it has never connected to this server before, and it wants to know if you trust the connection. The server has sent you it's 'key' which is used to decrypt the encrypted information it sends you. You almost certainly do trust the connection, and if you press 'Yes' PuTTY will store the key and not ask you this question again. If you pressed 'Yes' and it does ask you this question at some latter time, while making this connection, there is a possibility that someone is trying to intercept your password. That isn't very likely though, and you most likely will not have to worry about it. If you are asked this question again, check and see if anything has changed about the connection (maybe the server HAS changed it's key for a good reason, maybe you are trying to connect to a different machine than you thought) if you have tried it a couple of times and keep getting warnings about the key, and you suspect maybe someone IS trying to intercept your password, you should inform the helpdesk. If you press 'No' the connection will go through, but not store the key, and it will ask you this question next time you connect also. Cryptography is complicated! If you would like to understand it better, you could try starting here:
http://www.ssh.com/tech/crypto/intro.cfm
Short Answer: Press 'Yes' and forget about it.
6. Enter username and password After accepting the host key, the regular PuTTY terminal window will pop up. Enter your username and password (you will not see your password while you type it.)
7. UNIX! After you have logged in, you will find yourself at your regular UNIX prompt. From here on in, everything will work the same as it would have if you had used telnet. You can simply type 'pine' to launch the pine mail client. PuTTY/ssh does many many cool things which telnet was not capable of. For more information see the advanced PuTTY page. This page will also help you configure PuTTY if you are having problems with things like your backspace key not working or if you want to save your settings.
- 1365 views